Mobile Device Management (MDM) for Small Businesses Kyber Security
O Mobile Device Management (MDM), ou em português Gerenciamento de Dispositivos Móveis, é um software que permite gerenciar dispositivos móveis como smartphones, tablets e laptops, de forma remota, para controlar, proteger e ativar políticas de uso. Seu objetivo é otimizar e proteger o uso desses aparelhos, garantindo ao mesmo tempo a.. Mobile device management (MDM) is the administration of mobile devices, such as smartphones, tablet computers, and laptops.MDM is usually implemented with the use of a third-party product that has management features for particular vendors of mobile devices. Though closely related to Enterprise Mobility Management and Unified Endpoint Management, MDM differs slightly from both: unlike MDM, EMM.

Mobile Device Management w Google Workspace Fly On The Cloud

Mobile Device Support & Management OJ Networks IT Freshly Squeezed

Mobile device management with Microsoft Intune An introduction

Mobile Device Management

Mobile Device Management

Mobile Device Management
Mobile Device Management AGiiLE

Mobile Device Management Services Mobility Help Desk

Why Mobile Device Management Is Important For Your Business Nomerel Managed IT

Mobile Device Management NC Tech

Managed IT Services — Baker Tilly Technology Services
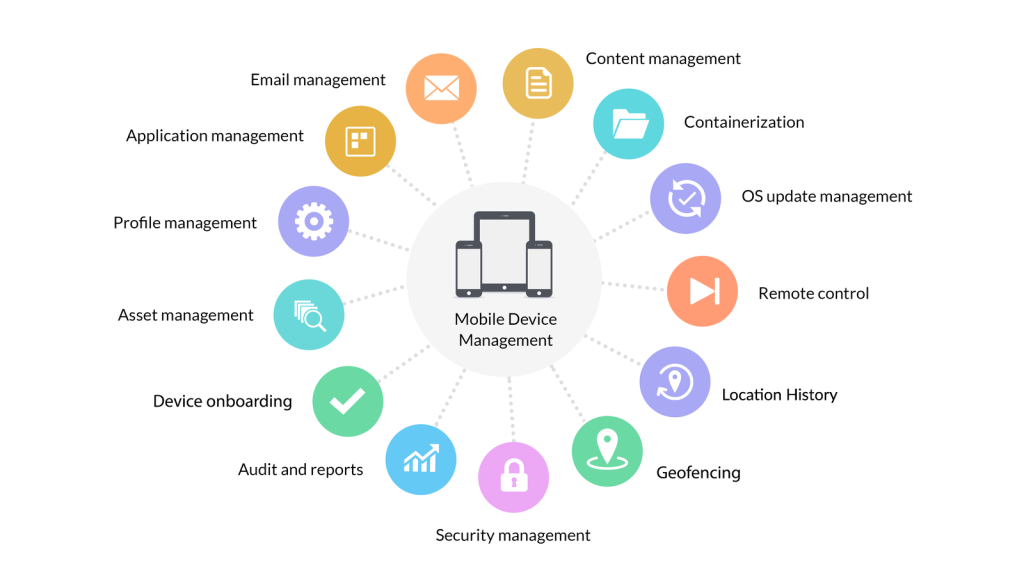
Apa Itu Mobile Device Management?

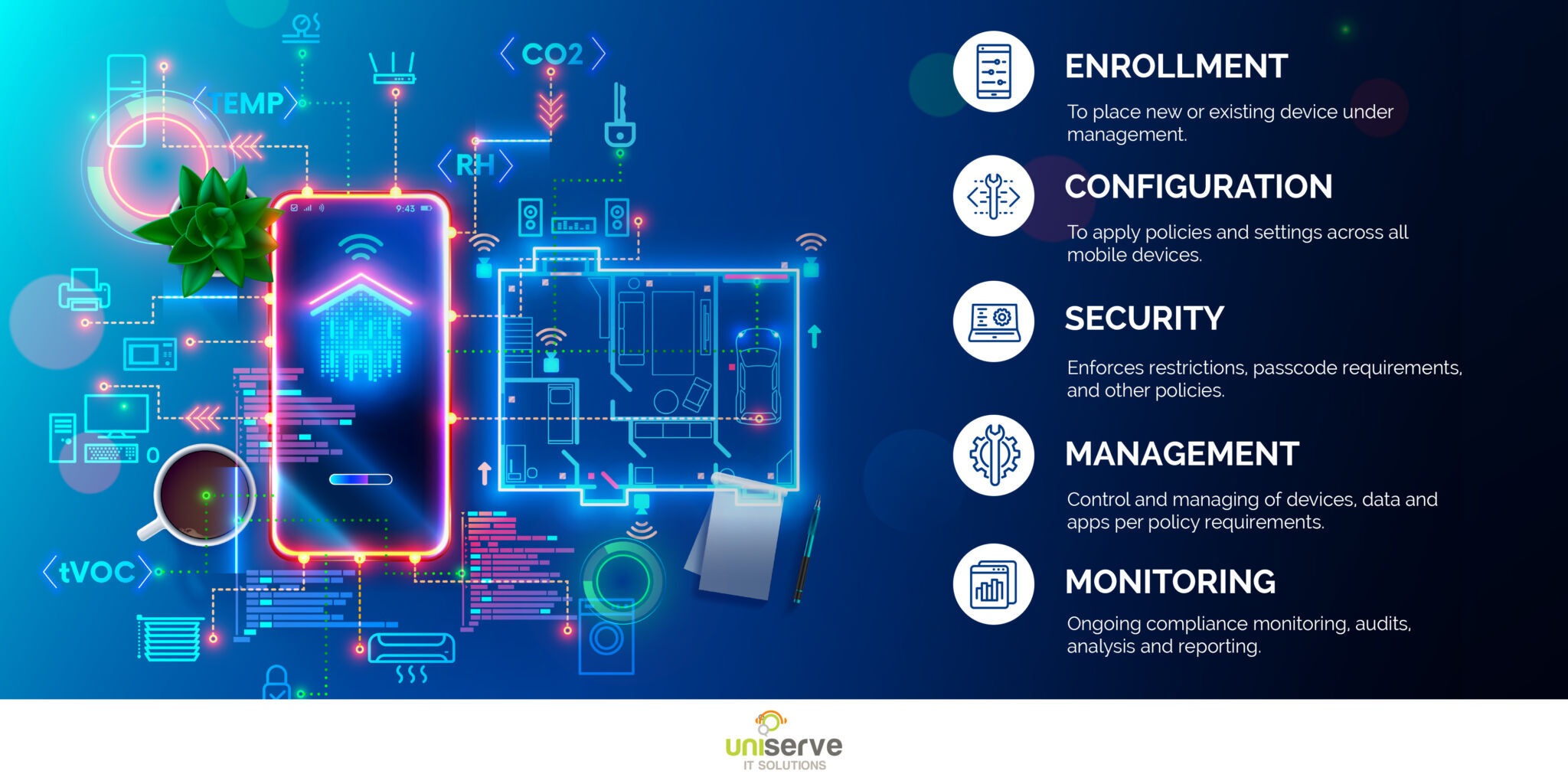
Mobile Device Management An Overview Uniserve IT Solutions

Mobile device management 101 Why it matters and how to deploy Vanta

Mobile Device Management

Best Mobile Device Management Solution

Mobile Device Management by SOTI YouTube
Mobile Device Management Mobile Device Management Software Ensures Data Security

What is Mobile Device Management?

What is Mobile Device Management (MDM)?
O Mobile Device Management (MDM) – em português, Gerenciamento de Dispositivos Móveis – é um software que permite gerenciar equipamentos como smartphones, ta.. O MDM é um tipo de solução que serve para monitorar, gerenciar e proteger dispositivos móveis, como celulares, tablets e notebooks, remotamente. Um MDM traz segurança e conformidade de dados aplicando códigos de acesso seguros, bloqueios de tela, perfis de trabalho, além de criptografar todo conteúdo confidencial.


